Azure Storage Security – File, Object, and Data Lake Storage
Azure Storage Security
Microsoft provides several layers of security to ensure that data stored in one of the Azure Storage services is protected from unauthorized access. As with any other data service in Azure, there are several network isolation and identity management options that can be used to limit who can access data in a storage account. The following sections examine the methods available for securing data in Azure Storage as well as some of the default security standards such as data encryption and protection from accidental deletes.
Network Isolation
Storage accounts have a public endpoint that provides access over the Internet. Azure allows users to isolate this endpoint by limiting access to certain IP addresses through a firewall, trusted Azure services, or specific Azure subnets. Azure also allows users to attach a private IP address from a VNet to a storage account, restricting communication to traffic that can access the VNet. This is the Microsoft recommended approach for securing storage accounts that store sensitive data such as personally identifiable information (PII).
All these options can be configured through the Azure Portal, or an Azure PowerShell or Azure CLI script after a storage account is created. Let’s walk through how to configure one of the network isolation options in the Azure Portal:
- Navigate to the storage accounts page in the Azure Portal and click on the storage account that was previously created.
- In the left-side panel of the storage account blade, click Networking. Figure 4.16 shows where this button is located.
FIGURE 4.16 Networking button
- There are three tabs listed at the top of the networking page: Firewalls And Virtual Networks, Private Endpoint Connections, and Custom Domain. We will cover the Firewalls And Virtual Networks and Private Endpoint Connections tabs for the purpose of configuring network isolation on a storage account. Just know that the Custom Domain tab allows you to map a custom domain to a blob or static website endpoint.
- The Firewalls And Virtual Networks tab enables users to allow access from specific VNets and subnets as well as specific IP addresses. Figure 4.17 illustrates these settings.
This tab also allows you to configure access from trusted Azure services and read access to storage logging and metrics from any network. There is also an option to determine whether traffic is routed over the Microsoft network or the Internet as it travels from the source application to the storage account’s public endpoint. These settings are illustrated in Figure 4.18.
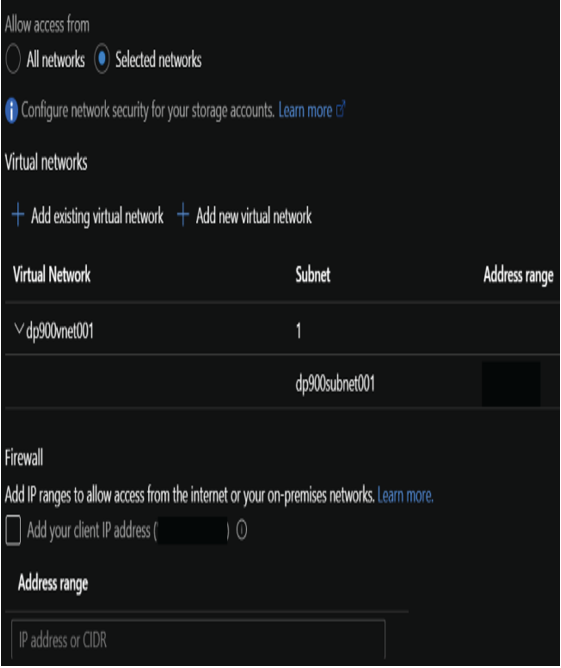
FIGURE 4.17 Virtual Network and Firewall Access
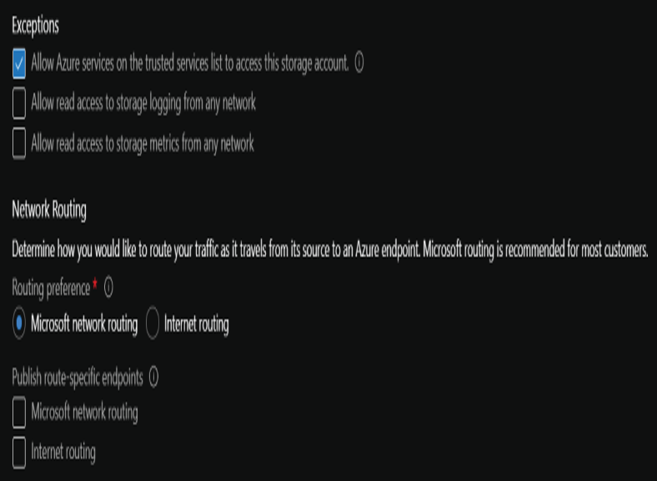
FIGURE 4.18 Exceptions and Networking Routing
